Settings contains permanent parameters, they are saved when the software is closed.
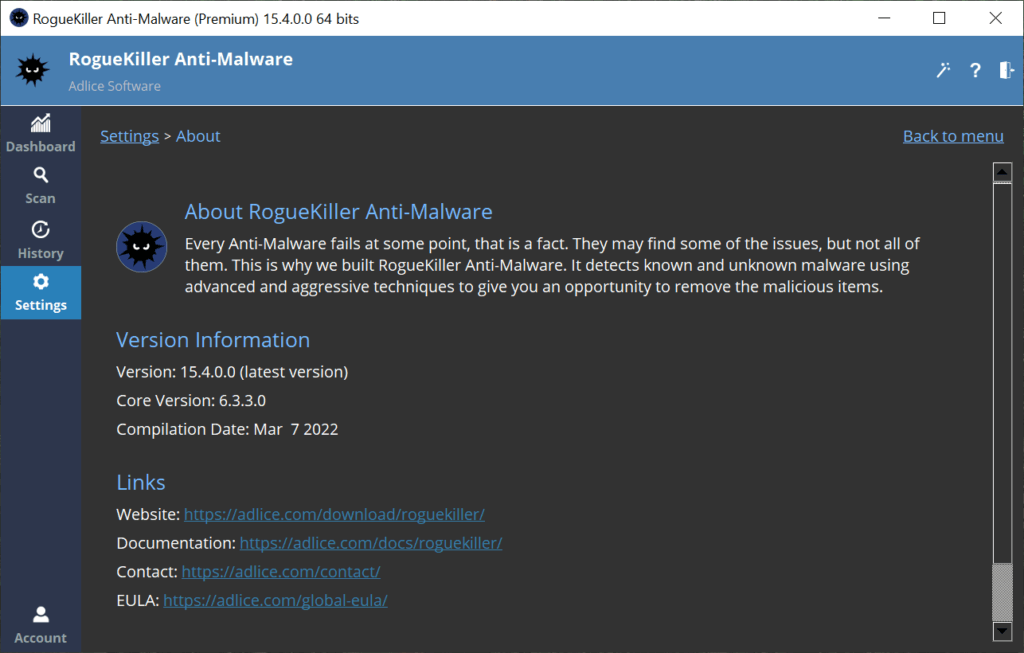
GENERAL SETTINGS
The General settings section gives the ability to change the following settings:
(Note: Some settings may be disabled if you use the Free version)
A. Telemetry: Send anonymous usage data to our server
B. Startup: Launch the software when the machine starts
C. Shell Extension: Enables the context menu in explorer
D. Notifications: Enables the software notifications
E. Automatic Updates: Enables self-updates when new version is available
F. Theme: Software theme (clear, dark, naked)
G. Language: Software language to use
H. Proxy: Proxy url (if any)
I. Agent: Agent configuration (if needed)
J. Rebranding: Change software/company name (Premium Tech only, please check documentation)
The “Default settings” button restores all values to default.
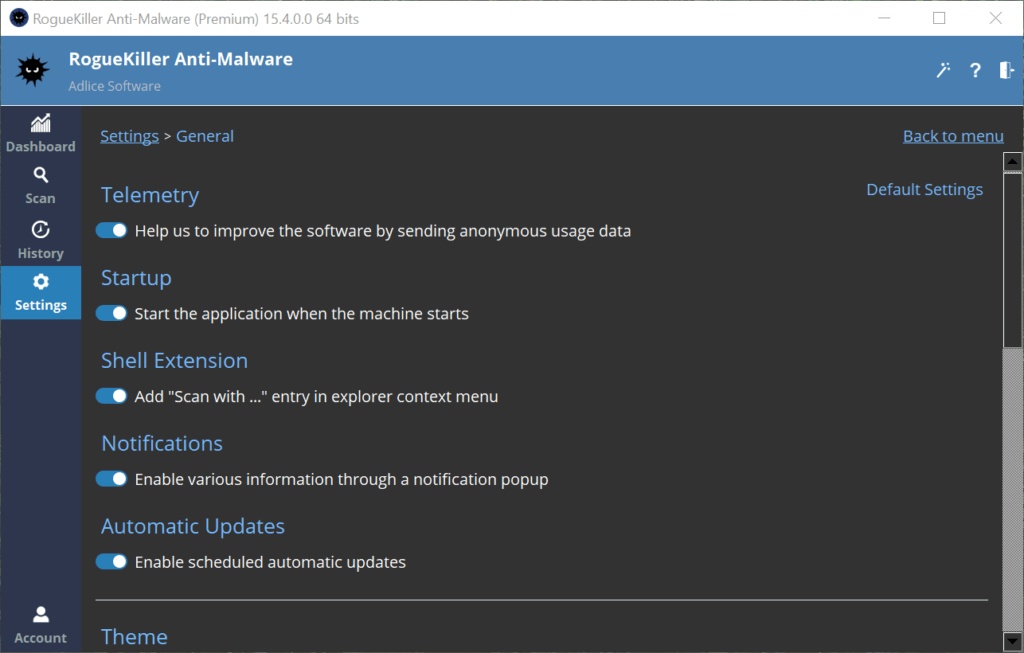
SCAN SETTINGS
The Scan settings section gives the ability to change the following settings:
(Note: Some settings may be disabled if you use the Free version)
A. Kernel Driver: Load kernel driver, may be needed to find/remove rootkits.
B. Archives Scan: Whether to scan archives (zip, 7z, rar, …) files.
C. Cloud Upload: Whether to send new files for analysis to our cloud server.
D. MalPE module: Agressive heuristics engine, Enable/Disable (BETA).
E. UCheck mini-scan: Before malware scanning, checks for software updates.
F. Scan full performance: Use full CPU resources during a scan. Scan is faster, but machine can be unresponsive.
The “Default settings” button restores all values to default.
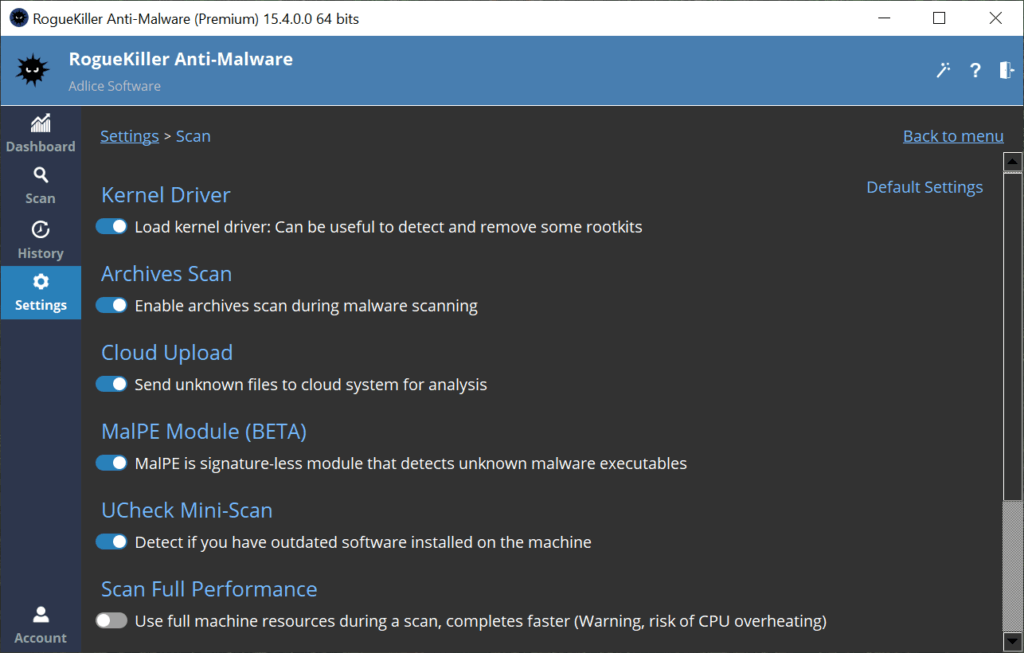
PROTECTION SETTINGS
The RTP settings section (starting with version 14) gives the ability to change the following settings:
(Note: Some settings may be disabled if you use the Free version)
A. Malware Protection: Enables the scan of executable files before they start.
B. Protected Storage: Enables the documents protection module, which prevents corruption of documents by ransomware.
C. Data Leak Prevention: Enables the DLP module, which prevents data theft of your documents by unauthorized programs.
D. Clipboard Protection: Enables the clipboard protection module, which prevents data theft in the clipboard by unauthorized programs (BETA).
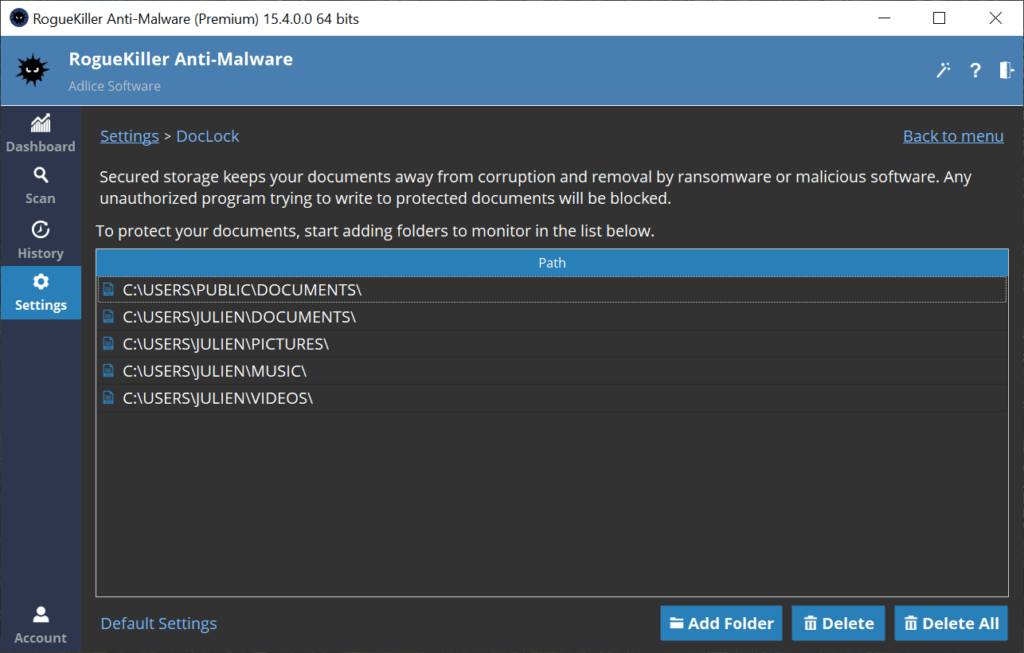
PROTECTED STORAGE
The “Protected Storage” section (starting with version 14) allows to configure the protected locations for the Documents Protection module. All documents in these locations will be monitored and protected against corruption by Ransomware.
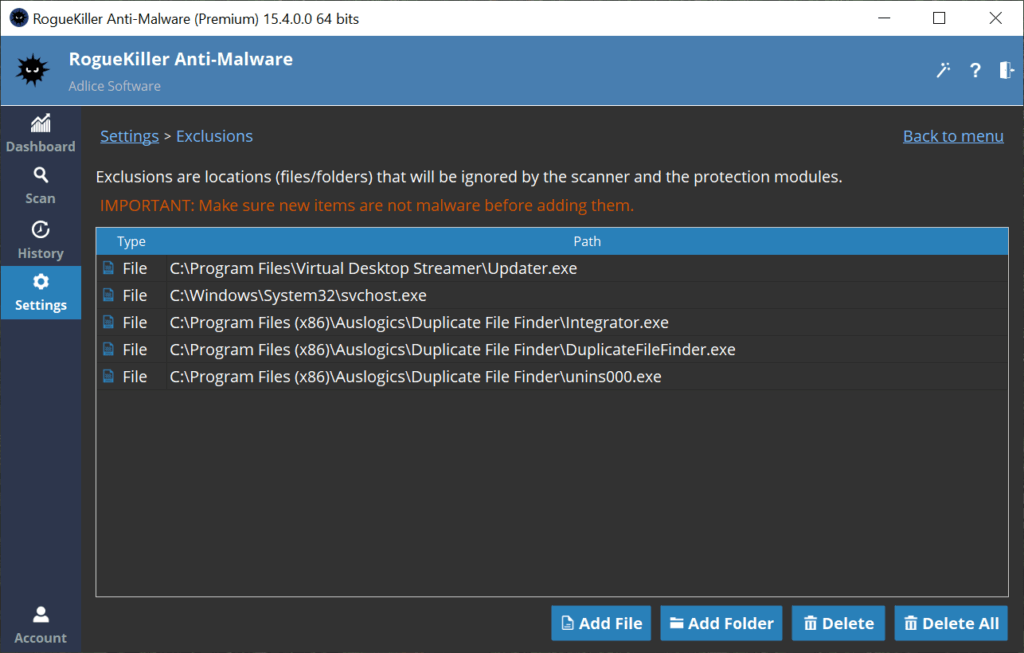
EXCLUSIONS
Exclusions are filesystem locations that the malware scanner will exclude. The exclusions can be added here or during a scan, and managed from here. For more information, please read the dedicated section.
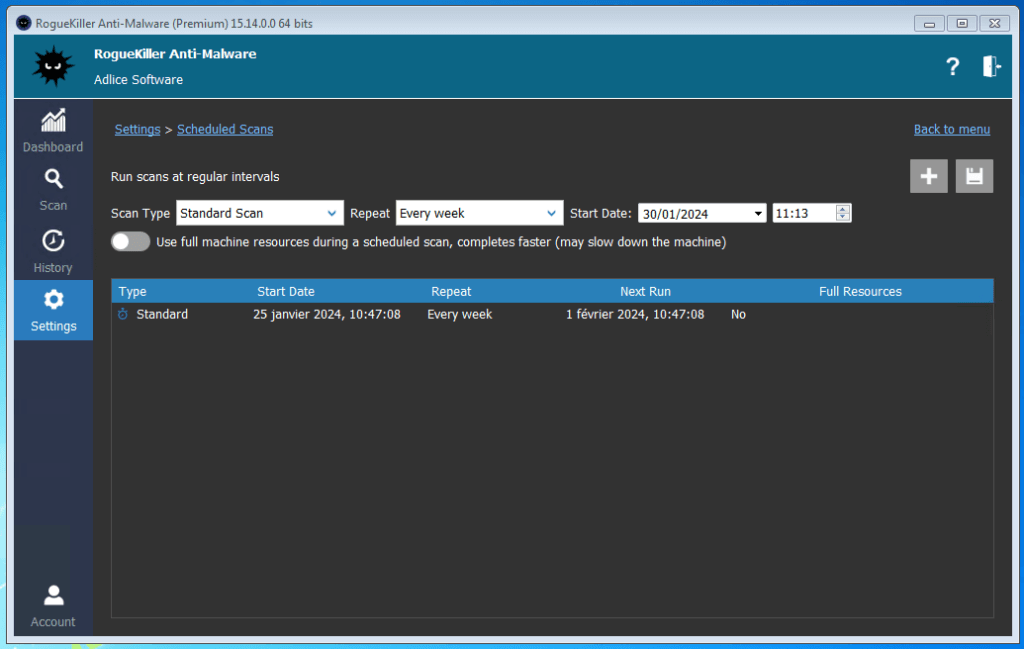
SCHEDULED SCANS
Scans (Standard, or Quick) can be scheduled on a regular basis (daily, weekly, …) and at a given time using the scheduler (Currently, only 1 allowed).
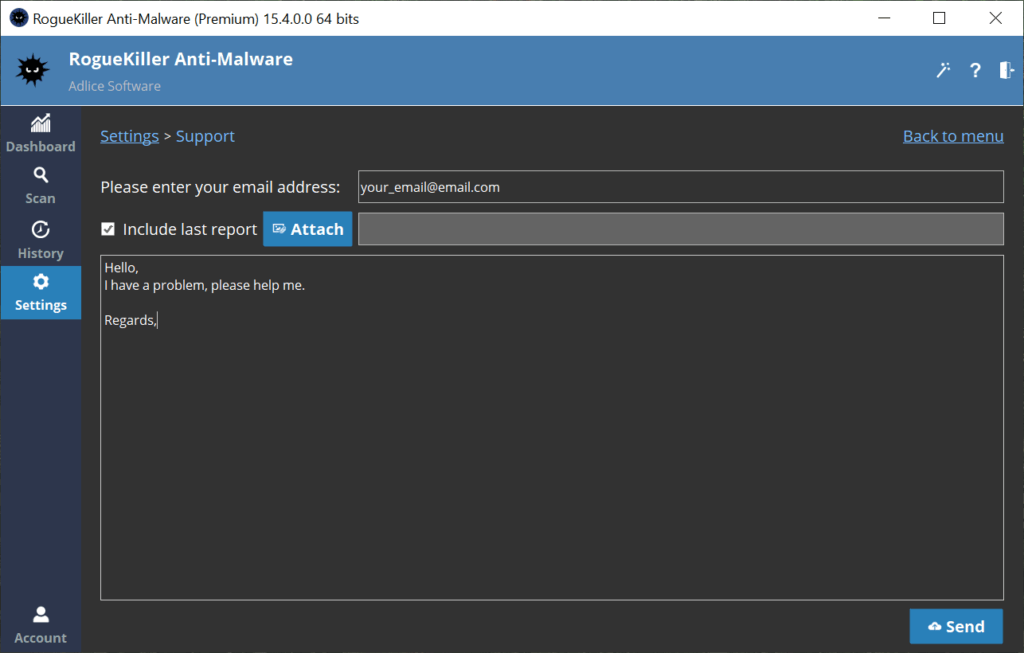
CONTACT FORM
The contact form (Premium only) allows to send an email inquiry without opening our website.
ABOUT SECTION
This sections describes the software and provides links to documentation and contact.