AVOID BEING HACKED: INTRODUCTION
With the development of broadband Internet connections, online/cloud-based services have become more and more numerous. Your data is not only located on your computer anymore but on a multitude of online servers. Not only you now should consider what could happen if your computer gets infected, but you must also consider what could happen if one of your online accounts gets compromised.
POSSIBLE ISSUES
- Data Theft. Your computer is infected by some malware or an online service is compromised, and the attacker stole private files that you REALLY do not want to be exposed online.
- Identity Theft. After an attacker has obtained specific data, they are able to impersonate yourself and use this for nefarious purposes.
- Data Loss. Some malware authors specialize in creating malware that are designed to encrypt the files on your computer and ask for a ransom to recover them. Data loss is not only linked to malicious activities, losing your laptop or catastrophic hard disk failures are also common causes.
All of the issues described above can be avoided most of the times with good practices. You can prevent your computer from being infected, and you can limit the damages if an online account is compromised. Let’s have a look how.
AVOID BEING INFECTED
UPDATE YOUR SOFTWARE
Software vulnerabilities can be used to install malware on your machine. Using only maintained software where such vulnerabilities are fixed is recommended against infection propagation. Also, making regular operating system and software updates is a strong advice to stay away from possible exploitations.
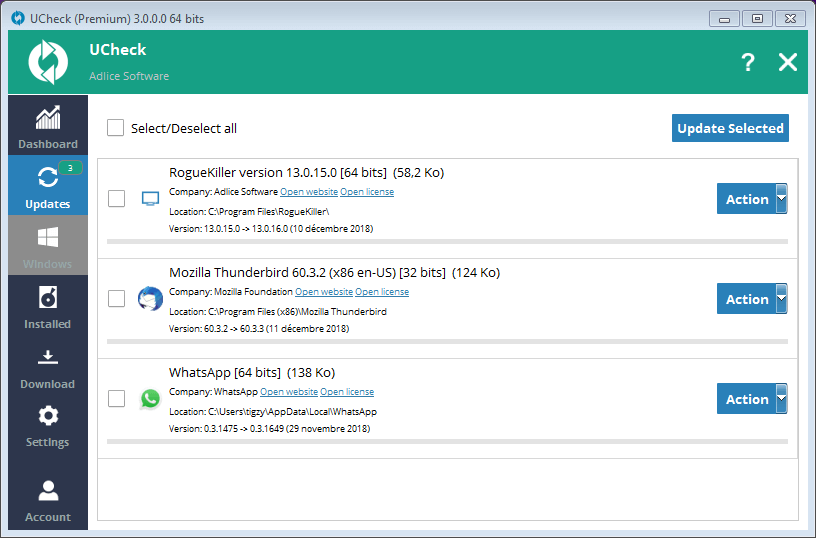
We recommend to download and install UCheck, and make regular scans and updates. If you are a Premium user, this is even easier if you enable the Automatic Software updates.
BLOCK (DANGEROUS) ADS
Many websites display advertisements, of multiple types: There is classic (non-intrusive) ads, the annoying ads (displaying pop-ups, misleading buttons and such) and the malicious ads. The later are (obviously) the most dangerous, they can scare the user with fake error messages or even download and install malware without any interaction (drive by download). If you block ads, you close another door.
Installing an ad blocker will prevent this kind of attack. We recommend uBlock Origin because of its effectiveness, low memory footprint, wide support and compatibility. Site note: please be responsible and deactivate the extension on websites you want to support.
INSTALL AN ANTIVIRUS + ANTIMALWARE
The antivirus is the first barrier of protection against malware when they have reached your computer, so it is important to install an effective one. If you are using Windows 10, Windows Defender Antivirus is our recommended one. If you are using an older version of Windows, Avira Free Antivirus or Kaspersky Security Cloud Free will be your choice. On Windows XP, Panda Dome Free Antivirus is the product you should use (with considering an upgrade…)
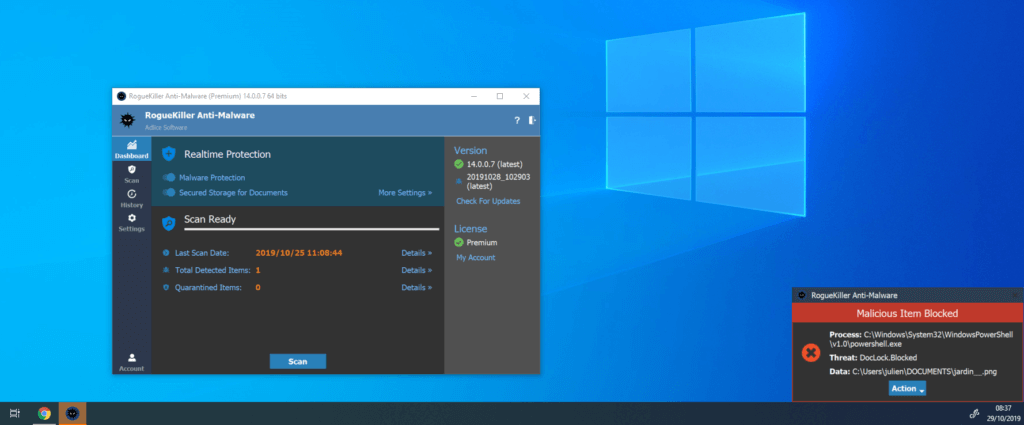
A second layer of protection is one based on heuristics (next-gen anti-malware) and is mostly used to prevent against unknown threat. Our flagship product RogueKiller Premium (starting at version 14) does quite the job and includes both malware protection and documents protection (to avoid your files being held for ransom).
NEVER OPEN ATTACHEMENTS FROM UNKNOWN SENDERS
Spam campaigns are still an important way to infect machines, usually under the form of Office documents containing malicious macros. If your antivirus does not detect malicious code in the attachment, that doesn’t mean it’s not malicious. As a rule of thumb, if you do not know the sender, do not click on any link contained in the email body or open attached files.
Another important rule is to never ever blindly trust what the received emails are saying. Most spam campaigns rely on social engineering using blackmail, bait or any technique to make people click on a link or open a file. The content may be scary, promising, or questionable. This is made on purpose, just move them to the junk folder.
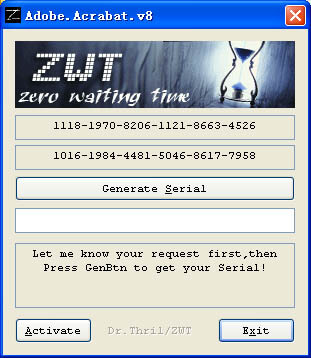
AVOID USING ACTIVATORS / CRACKS / KEYGENS
Software activators, or cracks/keygens are small pieces of software that promise you the use of a paid software for free. Generally speaking, 10% of them are working properly, 40% are buggy (but harmless) and 50% of them are pieces of malware, waiting to be executed.
Most of them also ask to turn off the Antivirus, so if you choose to activate a software with such a way it’s like playing “Russian Roulette”. Instead we recommend to either pay the software (look or ask directly for discounts), or use free alternatives (Linux, Open Office, …).
GOOD PRACTICES
NEVER USE THE SAME PASSWORD TWICE
Everytime you create a new account online, they ask you for an email and password. The password is most of the time encrypted on their end, but not always (due to poor practices).
If for some reason the service gets hacked, your email and password will be in the hands of hackers, who will try it on other services to hack all your accounts at once. This is why we recommend to never reuse a password. This is a hard advice, but we have solutions below so keep reading…
If you suspect an account is compromised, or just want to verify it’s not, you can search on haveibeenpwned with your email address.
USE A PASSWORD MANAGER
Remembering passwords is complicated, and impossible if you use 1 password per service (as recommended above). Fortunately there’s now services available on all devices (computer, smartphones, tablets…) that create and remember the passwords for you. They are even able to fill the forms for you, so that you don’t even need to copy or type it.
We don’t recommend storing passwords in the browser (like with Firefox), because it’s possible for hackers to steal the database files with all your passwords on your machine. Instead, we recommend cloud services like LastPass. You just need to remember one password (master password) to access and unlock your account, then your “vault” is accessible on all your devices.
USE 2FA WHEN POSSIBLE
2FA (for two-factor authentication) is a way to authenticate a user with something additional to its password. This additional verification is performed by using “something that only the user possesses”. Most of the time it’s a SMS received on a smartphone, or a token (hardware or software).
Some services provide a way to recognize 2FA authentification, which enforces the security of your account. If that’s the case we encourage you to enable it. Most popular (and stable) solutions for software token (unique codes randomly generated) are available for both Android and IPhone, Authy and Google Authenticator.
Important : Don’t forget to store your recovery codes when enabling the service.
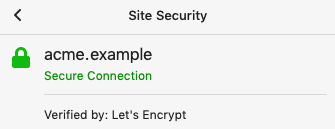
GREEN PADLOCK DOES NOT EQUAL SAFE
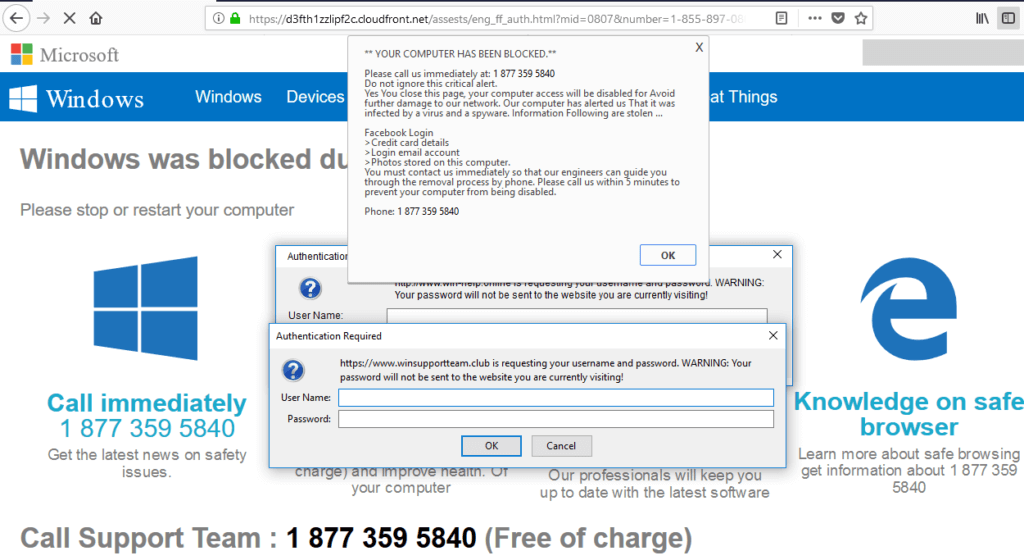
One of the common myths of Internet security is concerning the padlock displayed by the browser when visiting a website: if the padlock is closed and highlighted in green colour, the site is safe. In reality, the site MIGHT be safe, but it’s not always the case.
Malware author are using this myth to trick the users into trusting them. A green padlock means that the data transmitted between the computer and the website is encrypted, that’s it. The examples below are from a malicious website that tries to impersonate sophos.com.
BACKUP EARLY, BACKUP OFTEN
Backups are your safety wheel in case of trouble. They won’t help you not to crash, but they’ll definitely help you to recover. There’s 3 rules to follow with backups:
- Backup early (as soon as you have valuable data to save)
- Backup often (every day / week, depending on the amount and changes)
- Test your backups (verify they are properly saved and recoverable)
Nowadays there’s quite a few ways to backup your data: locally (with external drives or NAS) or by using a cloud service (Google Drive, Dropbox). Unfortunately, setting up one of these is not enough.
Whatever method you choose will still be vulnerable to hardware failure or unwanted data encryption (ransomware). If your NAS is available on the network a Ransomware will find it, same for a cloud account. An external drive can be stolen, burnt, or anything you can imagine.
A recommended way is to have at least 3 different backups (of the same data), in different locations:
- The first copy is stored on your local hard drive or on a NAS (working copy)
- The second copy is stored on a cloud storage service (online copy)
- The third copy is stored on an external hard drive, not connected to the network (offline copy)
We recommend Synology NAS and cloud services like Google Drive or Dropbox.