History of worm attacks
Computer worms were the second types of malware developed. At the beginning, like computer viruses, they were not designed to be malicious. One of them, called MORRIS, was designed to determine how large the Internet was (1988), but due to poor programmation ended damaging infrastructures and delete files. Some of them stay in memory like the infamous ILOVEYOU worm that destroyed the content of the infected computer and the SASSER worm that rebooted computers randomly.
How do computer worms spread ?
Computers worms are designed to leverage software vulnerabilities that allow them to gain control over an operating system, then scan the network for other vulnerable devices and so on. It’s quite difficult to remove a worm attack because, unless the vulnerability it uses to propagate is fixed beforehand, the worm will likely work back again in no time.

Worms attacks nowadays
Security in programming has become much drastic, leading to less vulnerabilities left unpatched or exploitable. However, sometimes a new worm is created and eventually makes headlines. Indeed, many devices (computers, but also connected objects) are now connected to the Internet and when a new worm hits, a huge botnet can be created in a very small time frame.
Recent computer worm infections
One of the most recent (May 2017) worm and the most famous one is WANNACRY. All operating systems running from Windows XP to Windows 10 were vulnerable and it’s estimated that over 300,000 computers were infected by the work in a time lapse of only four days.
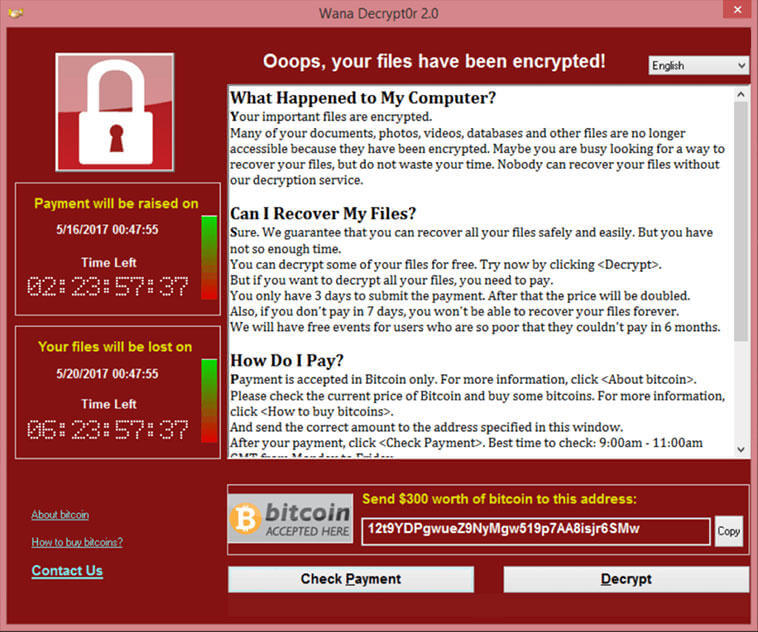
It used to install ransomware and it’s believed that the authors were paid around $150,000,000 by the victims.
How do I remove a worm ?
As stated before, computer worms method of propagation rely on software vulnerabilities. By keeping your system and your application updated, you greatly minimize the risk of being targeted by a computer worm. Adlice UCheck can help with you, fetching and always installing the latest versions of your software.
You can also install an antivirus software with a real-time protection, such as RogueKiller, to prevent malware from installing. If the malware is already in place you can also try our general malware removal guide.